ERROR: Backup of VM 1003 failed – CT is locked (snapshot-delete)
Solución:
qm unlock 100
pct unlock 801
dimarts, 11 de setembre del 2018
dilluns, 10 de setembre del 2018
Valoraci{o dels certificats https
3 págines per comprovar certificats i versions
https://securityheaders.com/?q=https%3A%2F%2Fassemblea.cat%2F&followRedirects=on
https://hstspreload.org/?domain=assemblea.cat
https://www.ssllabs.com/ssltest/analyze.html?d=assemblea.cat
https://timkadlec.com/2016/01/hsts-and-lets-encrypt/

Does the Let’s Encrypt client enable HSTS?
The Let’s Encrypt client can enable HSTS if you include the (currently undocumented) hsts flag.
./letsencrypt-auto --hsts
The reason why it’s not enabled by default is that if things go wrong HSTS can cause some major headaches.
Let’s say you have HSTS enabled. At some point something (pick a scary thing…any scary thing will do) goes wrong with your SSL configuration and your server is unable to serve a secure request. Your server cannot fulfill the secure request, but the browser (because of the HSTS header) cannot request anything that is insecure. You’re at an impasse and your visitor cannot see the content or asset in question. This remains the case until either your SSL configuration is restored or the HSTS header expires. Now imagine you’re running a large site with multiple teams and lots of moving parts and you see just how scary this issue could be.
Because of this risk, HSTS has to be an option that a user must specify in Let’s Encrypt—despite its importance.
https://gist.github.com/ebekker/abd89a833c050669cd5a
--hsts Add the Strict-Transport-Security header to every HTTP
response. Forcing browser to use always use SSL for
the domain. Defends against SSL Stripping. (default:
False)
--no-hsts Do not automatically add the Strict-Transport-Security
header to every HTTP response. (default: False)

https://securityheaders.com/?q=https%3A%2F%2Fassemblea.cat%2F&followRedirects=on
https://hstspreload.org/?domain=assemblea.cat
https://www.ssllabs.com/ssltest/analyze.html?d=assemblea.cat
https://timkadlec.com/2016/01/hsts-and-lets-encrypt/
Does the Let’s Encrypt client enable HSTS?
The Let’s Encrypt client can enable HSTS if you include the (currently undocumented) hsts flag.
./letsencrypt-auto --hsts
The reason why it’s not enabled by default is that if things go wrong HSTS can cause some major headaches.
Let’s say you have HSTS enabled. At some point something (pick a scary thing…any scary thing will do) goes wrong with your SSL configuration and your server is unable to serve a secure request. Your server cannot fulfill the secure request, but the browser (because of the HSTS header) cannot request anything that is insecure. You’re at an impasse and your visitor cannot see the content or asset in question. This remains the case until either your SSL configuration is restored or the HSTS header expires. Now imagine you’re running a large site with multiple teams and lots of moving parts and you see just how scary this issue could be.
Because of this risk, HSTS has to be an option that a user must specify in Let’s Encrypt—despite its importance.
https://gist.github.com/ebekker/abd89a833c050669cd5a
--hsts Add the Strict-Transport-Security header to every HTTP
response. Forcing browser to use always use SSL for
the domain. Defends against SSL Stripping. (default:
False)
--no-hsts Do not automatically add the Strict-Transport-Security
header to every HTTP response. (default: False)
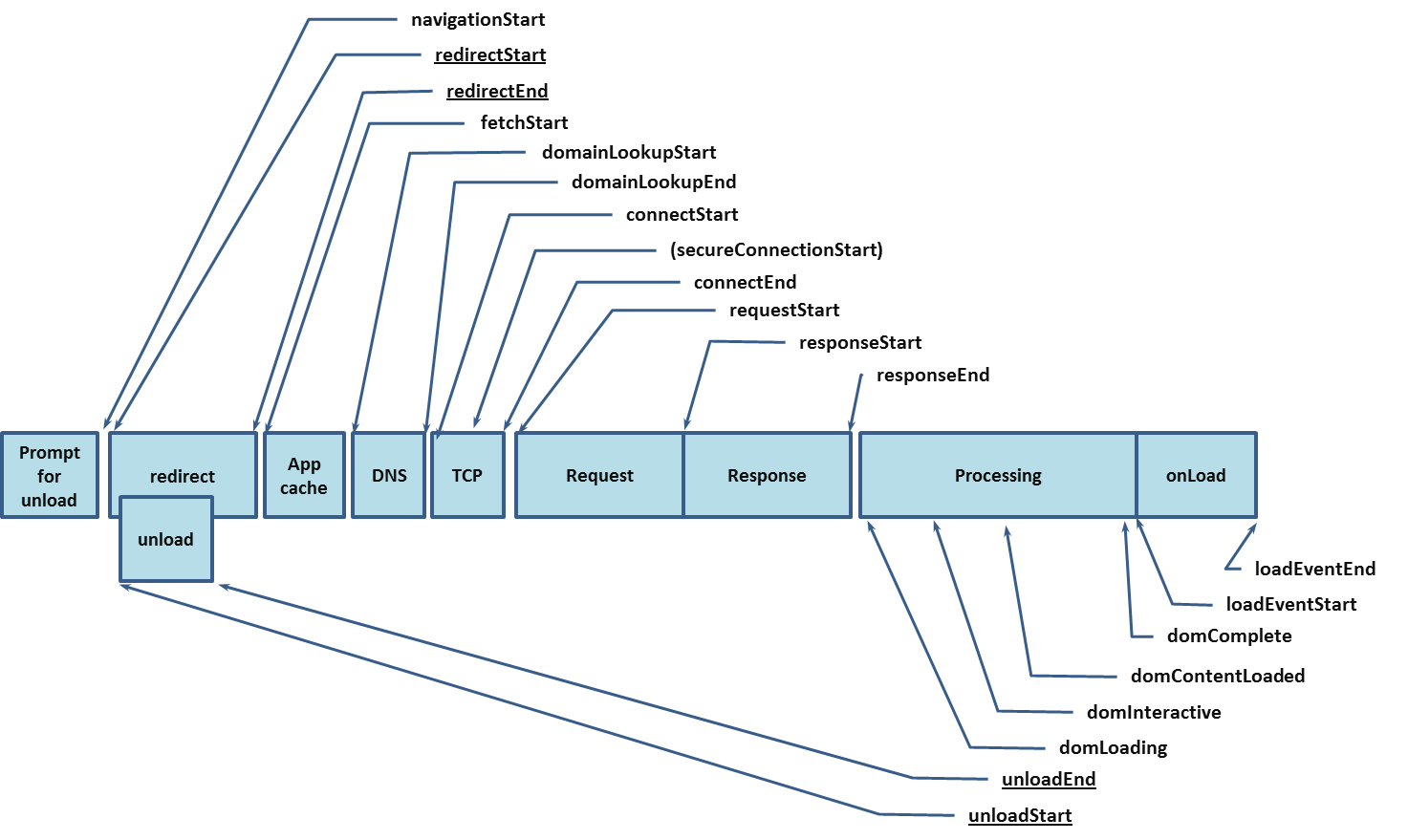
Navigation Timing
navigation-timing
https://www.w3.org/TR/navigation-timing/
Introduction
This section is non-normative.User latency is an important quality benchmark for Web Applications. While script-based mechanisms, such as the one described in [JSMEASURE], can provide comprehensive instrumentation for user latency measurements within an application, in many cases, they are unable to provide a complete end-to-end latency picture.
For example, the following script shows a naive attempt to
measure the time it takes to fully load a page:
The script calculates the time it takes to load the page after the
first bit of JavaScript in the head is executed, but it does not give any
information about the time it takes to get the page from the server. <!- Main page body goes from here. -->
http://.......cat/prova-navigation-timing.html
resultat
page loading time: 6
To address the need for complete information on user experience, this document introduces the
PerformanceTiming
interfaces. This interface
allows JavaScript mechanisms to provide complete client-side latency
measurements within applications. With the proposed interface, the previous
example can be modified to measure a user's perceived page load time.
The following script calculates how much time to load a page since the
most recent navigation.
The interface provided by this work does not intend to be used as any sort of
performance benchmark for user agents.<!- Main page body goes from here. -->
http://.......cat/prova-navigation-timing2.html
resultat
User-perceived page loading time: 54
continuant del document
https://www.w3.org/TR/navigation-timing/timing-overview.png
https://developers.google.com/web/fundamentals/performance/navigation-and-resource-timing/
m'he de mirar el contingut
https://github.com/micmro/performance-bookmarklet
https://github.com/andydavies/waterfall
pero finalment he anat a web de proves de temps de carrega
https://www.webpagetest.org/
Web Page Performance Test for
ies-sabadell.cat
From: Dulles, VA - Chrome - Cable
10/9/2018, 10:01:42
10/9/2018, 10:01:42
- Summary
- Details
- Performance Review
- Content Breakdown
- Domains
- Processing Breakdown
- Screen Shot
- Image Analysis
- Request Map
Tester: VM2-01-192.168.11.98
First View only
Test runs: 3
First View only
Test runs: 3
Performance Results (Median Run)
| Document Complete | Fully Loaded | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Load Time | First Byte | Start Render | Speed Index | First Interactive (beta) | Time | Requests | Bytes In | Time | Requests | Bytes In | Cost | |
| First View (Run 2) | 21.449s | 1.432s | 3.600s | 4039 | 10.070s | 21.449s | 137 | 10,747 KB | 21.652s | 138 | 10,748 KB | $$$$$ |
https://testmysite.withgoogle.com/intl/en-gb
https://frontal.ies-sabadell.cat/cicles-moodle
Loading time:
This is Speed Index, how long the visible content of your page takes to appear using Chrome on a Moto G4 device within a 3G network. Loading time can vary based on server location, device, browser, and third-party apps. If your site contains carousels, overlays or interstitials, this may impact your loading time results. To perform a website speed test using different settings, visit webpagetest.org.
Estimated visitor loss:
This is the probability of a user leaving this web page as a result of waiting for more than three seconds for it to load. [Source]
This is Speed Index, how long the visible content of your page takes to appear using Chrome on a Moto G4 device within a 3G network. Loading time can vary based on server location, device, browser, and third-party apps. If your site contains carousels, overlays or interstitials, this may impact your loading time results. To perform a website speed test using different settings, visit webpagetest.org.
Estimated visitor loss:
This is the probability of a user leaving this web page as a result of waiting for more than three seconds for it to load. [Source]
5s
Loading time on 3G: Good19%
Est. Visitor loss
(Due to loading time)
altres
https://developers.google.com/speed/pagespeed/insights/?url=ies-sabadell.cat&tab=mobile
https://developers.google.com/speed/pagespeed/insights/?url=ies-sabadell.cat&tab=desktop
maltrail ofereix aquesta informació
http://check.googlezip.net/e2e_probe?q=76444f89-1459-487e-bbce-02bb2d7a6e05
10.1.133.208

| 39691 | 216.58.211.108  | 80 (http) | TCP | HTTP | potential proxy probe (suspicious) | (heuristic) |
un ordinador a la xarxa wifi que vol connectra a googlezip.net
i no se que és?
cercant per google
https://developer.chrome.com/multidevice/data-compression-for-isps
Chrome Data Compression Proxy for Network Administrators, Carriers, and ISPs
Details
When Chrome starts with the DCP setting enabled, the DCP is enabled by the user, or a network interface change occurs, Chrome asynchronously issues an in-the-clear HTTP request to the canary URL,http://check.googlezip.net/connect.
There are three possible outcomes of the canary URL request:
- If the response status code is 200 and the response body is
OK, Chrome uses an encrypted proxy connection for subsequent HTTP requests. - If the response status code is anything other than 200 or the response
body is anything other than
OK, Chrome uses an unencrypted proxy connection. - If the canary URL request times out or a DNS error occurs, Chrome uses an encrypted proxy connection.
Proxy Bypass
The Chrome DCP issues a proxy bypass response for URLs matching a list of restricted URLs maintained by Google. A proxy bypass causes Chrome to disable the use of SSL for the DCP connection for a short time (randomly chosen between 1 and 5 minutes). Carriers or network administrators can then block or take appropriate action on the request.Proxy Bypass is used mainly for:
- Child sexual abuse material, which includes NCMEC, IWF and other lists used globally by Google for restricting access to such illegal material
- URLs subject to court-ordered DMCA and other takedowns on Google services
- Country-specific takedown lists, which are applied only to users with IP addresses originating in the associated country
- A small number of other sites known not to work well with the DCP (e.g., known carrier billing portal and intranet sites)
més
https://support.opendns.com/hc/en-us/articles/227989047-Chrome-for-Mobile-and-OpenDNS-Inconsistency-with-block-pages
Overview
If you're seeing issues with inconsistent block page issues with Chrome for Mobile, please have your end user disable Chrome's Reduce Data usage feature. As an example, you may see certain pages being blocked in Chrome for Mobile when they are not blocked on another browser on the same mobile device or allowed when unexpected.
When this feature is enabled, all HTTP traffic from Chrome for Mobile gets redirected to a Google proxy at this address: compress.googlezip.net. The proxy then compresses the data and sends it back to the client. Unfortunately, when this happens, the proxy will perform it's own DNS requests against it's own DNS servers, which causes inconsistent block page issues as the DNS services are no longer with OpenDNS.
multiples reports podem trobar
https://www.fastvue.co/sophos/blog/google-data-saver-affect-security-confidentiality-reporting
How Google Data Saver affects web traffic logging and reporting
As you can imagine, Google Data Saver can cause havoc with your reporting as well.Below are two screenshots from an Activity Report I generated using Fastvue Sophos Reporter to illustrate the effects. The first with Google Data Saver turned off, and the second with Google Data Saver turned on.
Google Data Saver Off
 When accessing fastvue.co with Google Data Saver off, the HTTP
content is correctly served from fastvue.co and logged and reported
appropriately.
When accessing fastvue.co with Google Data Saver off, the HTTP
content is correctly served from fastvue.co and logged and reported
appropriately.Google Data Saver On
 With Google Data Saver turned on, all of the individual HTTP requests
are gone, and all you see are HTTPS sessions to
https://proxy.googlezip.net
With Google Data Saver turned on, all of the individual HTTP requests
are gone, and all you see are HTTPS sessions to
https://proxy.googlezip.netControlling Google Data Saver
Now you understand how Google Data Saver affects your visibility and control over your web traffic, you may be wondering how you can disable it in your network.COMPROBEM A CASA AMB FIREFOX
http://check.googlezip.net/test.html
Chrome Compression Proxy not detected.
Response headers for the AJAX request to //check.googlezip.net/probe/image.jpg:
Accept-Ranges: bytes
Content-Type: image/jpeg
Access-Control-Allow-Origin: *
access-control-expose-headers: Via, X-Original-Content-Length, Chrome-Proxy
Content-Length: 643
Date: Mon, 10 Sep 2018 07:40:08 GMT
Pragma: no-cache
Expires: Fri, 01 Jan 1990 00:00:00 GMT
Cache-Control: no-cache, no-store, must-revalidate
Last-Modified: Thu, 21 Apr 2016 03:17:22 GMT
X-Content-Type-Options: nosniff
Server: sffe
x-xss-protection: 1; mode=block
Navigation timings:
dns: 0
con: 0
req: 34
rcv: 0
ntsrt: 68
nsfs: 2
ntplt0: 128
vull realment que al centre s'utilitzi el proxy per saltar els controls de navegació a google ?
diumenge, 11 de febrer del 2018
password - contrasenya ntopng
canvi de la contrasenya de admin de ntopng
posem la contrasenya admin a admin
>echo -n "admin" | md5sum
21232f297a57a5a743894a0e4a801fc3 -
Notice that the
>redis-cli SET ntopng.user.admin.password 21232f297a57a5a743894a0e4a801fc3
comprovem de nou
root@zentyal:/home/ies# redis-cli get ntopng.user.admin.password
"21232f297a57a5a743894a0e4a801fc3"
tinc dos intal·lacions de ntopng en diferents rutes en dos ordinadors amb el mateis so
whereis ntopng
ntopng: /usr/local/bin/ntopng /usr/share/ntopng
whereis ntopng
ntopng: /usr/sbin/ntopng /etc/ntopng.conf /usr/share/ntopng /usr/share/man/man8/ntopng.8.gz
/usr/local/bin/ntopng -i eth0 -i eth4 -w 3001 -L -d &
o
/usr/sbin/ntopng -i eth2 -w 3001 -L -d &
depenent de l'ordinador
posem la contrasenya admin a admin
>echo -n "admin" | md5sum
21232f297a57a5a743894a0e4a801fc3 -
Notice that the
-n is mandatory. Without it, your hash will be totally wrong since it includes the newline character>redis-cli SET ntopng.user.admin.password 21232f297a57a5a743894a0e4a801fc3
comprovem de nou
root@zentyal:/home/ies# redis-cli get ntopng.user.admin.password
"21232f297a57a5a743894a0e4a801fc3"
tinc dos intal·lacions de ntopng en diferents rutes en dos ordinadors amb el mateis so
whereis ntopng
ntopng: /usr/local/bin/ntopng /usr/share/ntopng
whereis ntopng
ntopng: /usr/sbin/ntopng /etc/ntopng.conf /usr/share/ntopng /usr/share/man/man8/ntopng.8.gz
/usr/local/bin/ntopng -i eth0 -i eth4 -w 3001 -L -d &
o
/usr/sbin/ntopng -i eth2 -w 3001 -L -d &
depenent de l'ordinador
dissabte, 20 de gener del 2018
reinici serveis zentyal 5.0
en versió 3.5 feiem
service zentyal firewall restart
ara en versió 5 hem de fer
zs squid restart
recordar que per regla tallafocs personalitzades tenim
/etc/zentyal/hooks/firewall.postservice
i que tenim un
/etc/zentyal/stubs/squid/ per tal de no tocar /usr/share/zentyal/stubs/squid
service zentyal firewall restart
ara en versió 5 hem de fer
zs squid restart
recordar que per regla tallafocs personalitzades tenim
/etc/zentyal/hooks/firewall.postservice
i que tenim un
/etc/zentyal/stubs/squid/ per tal de no tocar /usr/share/zentyal/stubs/squid
diumenge, 6 d’agost del 2017
proxmox montar recurs lxc a l'arrancada
sobre la proxmox montar en un directore
mount -t nfs 192.168.1.250:/mnt/externovolumen /mnt/bindmounts/shared/
al contenidor lxc 167
pct set 167 -mp0 /mnt/bindmounts/shared/,mp=shared
pct start 167
pct enter 167
root@moodle2ubu16remote:~# mount|grep shared
192.168.1.250:/mnt/externovolumen on /shared type nfs (rw,relatime,vers=3,rsize=131072,wsize=131072,namlen=255,hard,proto=tcp,timeo=600,retrans=2,sec=sys,mountaddr=192.168.1.250,mountvers=3,mountport=740,mountproto=udp,local_lock=none,addr=192.168.1.250)
mount -t nfs 192.168.1.250:/mnt/externovolumen /mnt/bindmounts/shared/
al contenidor lxc 167
pct set 167 -mp0 /mnt/bindmounts/shared/,mp=shared
pct start 167
pct enter 167
root@moodle2ubu16remote:~# mount|grep shared
192.168.1.250:/mnt/externovolumen on /shared type nfs (rw,relatime,vers=3,rsize=131072,wsize=131072,namlen=255,hard,proto=tcp,timeo=600,retrans=2,sec=sys,mountaddr=192.168.1.250,mountvers=3,mountport=740,mountproto=udp,local_lock=none,addr=192.168.1.250)
root@moodle2ubu16remote:~# cd /shared/
root@moodle2ubu16remote:/shared# ls
hola servidorweb
si no està montat al servidor proxmox, en el moment que estigui montat ja està accesible
recomanacions o advertència
The contents of device mount points are not backed up when using vzdump.
Subscriure's a:
Missatges (Atom)